Accenture’s Latest Innovations in Consulting
Accenture’s Metaverse Practice: Shaping the Future of Business
Accenture is heavily investing in the metaverse, offering consulting services to help businesses navigate this emerging digital landscape. They aren’t just dipping their toes in; they’re building comprehensive strategies for clients, covering everything from initial metaverse strategy development and technology implementation to operationalizing metaverse initiatives and measuring ROI. This involves understanding the unique opportunities and challenges the metaverse presents for different industries and developing tailored solutions that leverage its potential for innovation and growth. Their approach emphasizes a human-centric design, ensuring that metaverse applications are both effective and user-friendly.
AI-Powered Solutions for
Understanding the Earn It Act Implications & Impact
Introduction:
The Earn It Act has stirred a whirlwind of debate and speculation within legal and tech circles. Introduced as a measure to combat online child exploitation, its implications extend far beyond its initial intentions. Understanding the Earn It Act requires a deep dive into its provisions, potential impacts, and the broader implications for online privacy and security.
The Purpose Behind the Earn It Act:
At its core, the Earn It Act aims to hold online platforms accountable for facilitating the spread of child sexual abuse material (CSAM). By conditioning Section 230 immunity on compliance with best practices outlined by
Autonomous Vehicles Data Privacy: Navigating Digital Roads

Navigating Digital Roads: Autonomous Vehicles Data Privacy
Autonomous vehicles, heralded as the future of transportation, raise critical questions about data privacy. As these vehicles become more prevalent, safeguarding the privacy of the data they generate is paramount. In this article, we delve into the complexities of autonomous vehicles data privacy, exploring challenges, regulatory considerations, and the path forward in ensuring secure and responsible use of data.
Data-Driven Autonomy: A Privacy Conundrum
The advent of autonomous vehicles has ushered in an era where vehicles are not just modes of transportation but also data-generating entities. From sensor data to location information, the
Navigating Cybersecurity Incidents: Effective Response Strategies
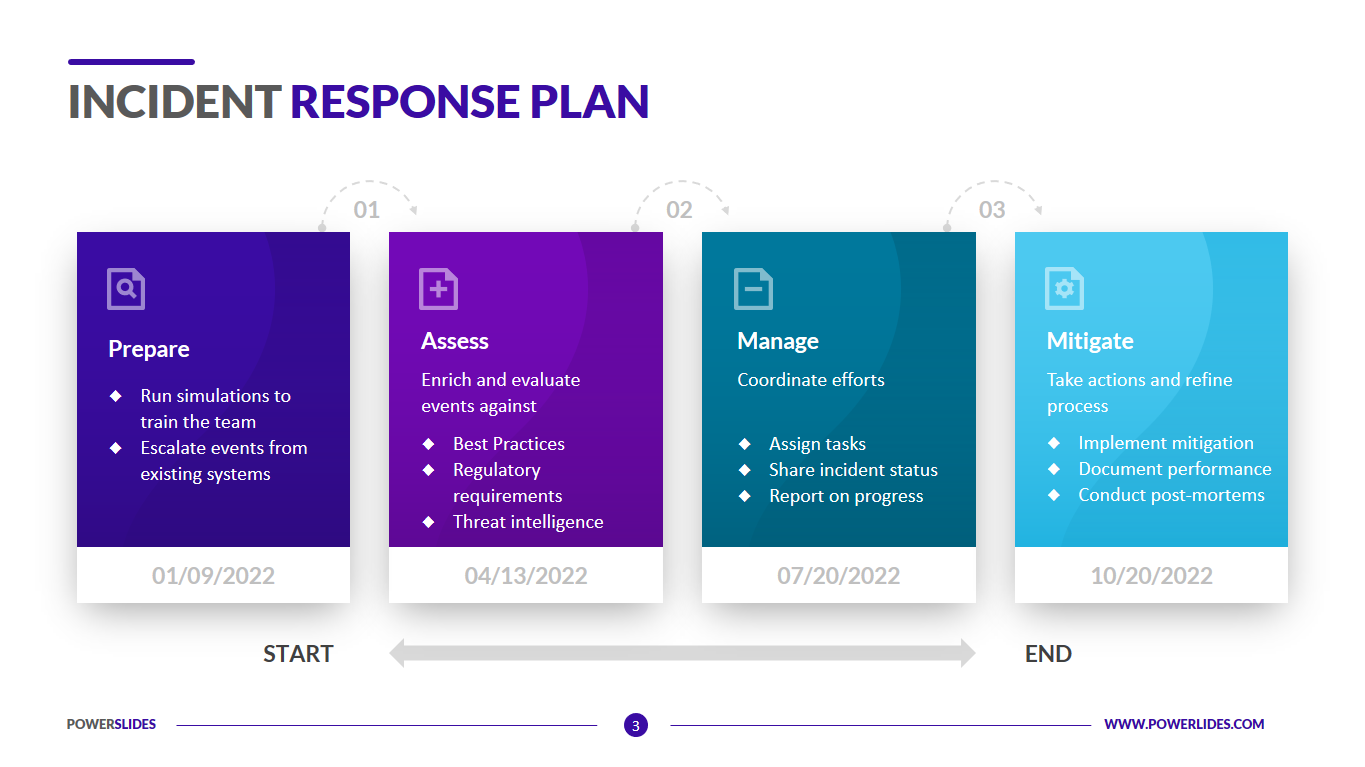
Navigating Cybersecurity Incidents: Effective Response Strategies
The ever-evolving landscape of cybersecurity presents businesses with both opportunities and challenges. With the increasing frequency and sophistication of cyber threats, having a robust incident response plan is essential for organizations to mitigate potential damage. In this article, we explore the importance of cybersecurity incident response plans and effective strategies for navigating through cyber threats.
Understanding the Cybersecurity Landscape
In today’s interconnected digital world, the threat landscape is diverse and constantly evolving. Cyberattacks can come in various forms, from ransomware and phishing attacks to sophisticated nation-state threats. Understanding the intricacies of the cybersecurity landscape
Strategic Cybersecurity Risk Management: Safeguarding Digital Assets

Safeguarding Digital Assets: Strategic Cybersecurity Risk Management
Cybersecurity risk management is a critical component of modern business operations, especially as organizations become increasingly reliant on digital technologies. In this article, we explore the significance of strategic cybersecurity risk management in protecting valuable digital assets, addressing evolving threats, and ensuring the resilience of businesses in the face of cyber challenges.
The Growing Importance of Cybersecurity
As the digital landscape expands, so does the threat landscape. Cybersecurity has become a top priority for organizations globally, recognizing the potential impact of cyber threats on operations, reputation, and financial stability. Cybersecurity risk management is
Connecting the Future: Advancements in Telecommunications Infrastructure

Connecting the Future: Advancements in Telecommunications Infrastructure
In our digitally connected world, the backbone of seamless communication and data exchange lies in robust telecommunications infrastructure. As technology continues to evolve, so does the need for cutting-edge infrastructure to support the increasing demands of a hyper-connected society.
The Evolution of Telecommunications Infrastructure
Telecommunications infrastructure has come a long way from traditional landline networks to the sophisticated, high-speed systems we rely on today. The evolution encompasses a transition from copper wires to fiber optics, enabling faster data transmission and supporting a myriad of services, including voice, video, and data.
Fiber Optics Revolutionizing
Safeguarding Legal Information: Effective Data Privacy Solutions

Navigating the Legal Landscape: The Imperative of Data Privacy Solutions
In the intricate world of legal affairs, protecting sensitive information is a non-negotiable aspect of maintaining trust and integrity. Legal data privacy solutions have become paramount, offering robust measures to safeguard confidential data in an era of digital information exchange.
Understanding the Need for Data Privacy in the Legal Sector
Confidentiality in Legal Matters
Legal professionals handle an abundance of sensitive information, from client details to case strategies. Maintaining the confidentiality of such data is not only an ethical obligation but a legal requirement. Data privacy solutions provide a shield


